I was at the Colorado School of Mines on Saturday for a Science Olympiad competition my daughter was participating in. By all accounts Mines is a good school and we've had many graduates of the high school I teach at continue their education there and love it, and it's a beautiful campus.
In many ways, Science Olympiad is like a track or swim meet, a whole lot of waiting around until your event begins. In my daughter's case, she was in two events, right in the middle of the day, only one of which I was allowed to watch. So I had a spare eight hours or so to fill. Naturally I brought some books to read and a laptop, figuring I could hop on their wifi and get some work done. Conveniently School of Mines does have a guest network setup where they give you a guest login credential for temporary access. The only problem - they wouldn't give us the login credentials.
According to the person we talked to, it would be a "security risk" and a "liability issue" if they allowed us to use their network. Now, I don't know the details of their network, but I was a bit surprised by this, given that my public, K-12 school district has a guest wireless network available to anyone with no login credentials needed. Here they are hosting thirty teams from around the state, grades 6-12, and their parents, and the way you say "welcome" to these prospective students (this was Science Olympiad, after all, at a math/science/engineering college) is "we don't trust you to use our network?" (And, of course, the students were pretty busy, it would've been mostly parents and the teacher-sponsors using the network.)
But, I was polite, and returned to the classroom that was our home base . . . where I noticed that the teacher computer was turned on and logged into the network. Not only was it logged into the network, but it was also logged into the professor's home directory on the server and his Mines email account. So I proceeded to periodically use that machine throughout the day to check email and do a little bit of work.
What I briefly considered, but then refrained from doing, was emailing the CIO of the university (and copying the President) - from the professor's email account, of course - and pointing out that perhaps giving guest wireless access to prospective students and their parents was not the security or liability issue they should be most worried about. (And, no, I did not read any of the professor's email - although I did notice he had over 4000 unread messages . . .)
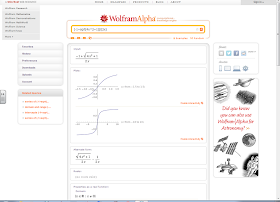
The second thing I learned at college on Saturday is in a slightly different vein. When I launched the browser on that teacher machine the professor apparently has it set to automatically open the tabs that were previously open. Here are screenshots of the three tabs that opened:
One was in the professor's Google Drive account, open to a PDF of a research article. The second was open to Wolfram Alpha, with a graph of an interesting square root function. And the third was open to a Wikipedia article about the Munsell Color System.
I don't want to read too much into which tabs were open, because I lack the context of knowing what the professor was doing with the information. But I think asking some questions about these open tabs would make for an interesting discussion in your school, and particularly in your high school math department.
For example, one might ask, "What implications might there be for your high school math curriculum (and classes) when a math professor at a high-end science and engineering school like the Colorado School of Mines has Google Drive, Wolfram Alpha, and Wikipedia open in his web browser?"
Or maybe you'd phrase it slightly differently, something along the lines of, "For the very small portion of your high school students who are going on to major in math/science/engineering in college, what should you be doing in your classes to prepare them for college math classes that utilize Google Drive, Wolfram Alpha, and Wikipedia?"
I imagine you can think of a few more questions as well, but I think it just might be a discussion worth having. As is a discussion surrounding, "If you have wireless, but you don't let anyone use it, is it really there?"


No comments:
Post a Comment